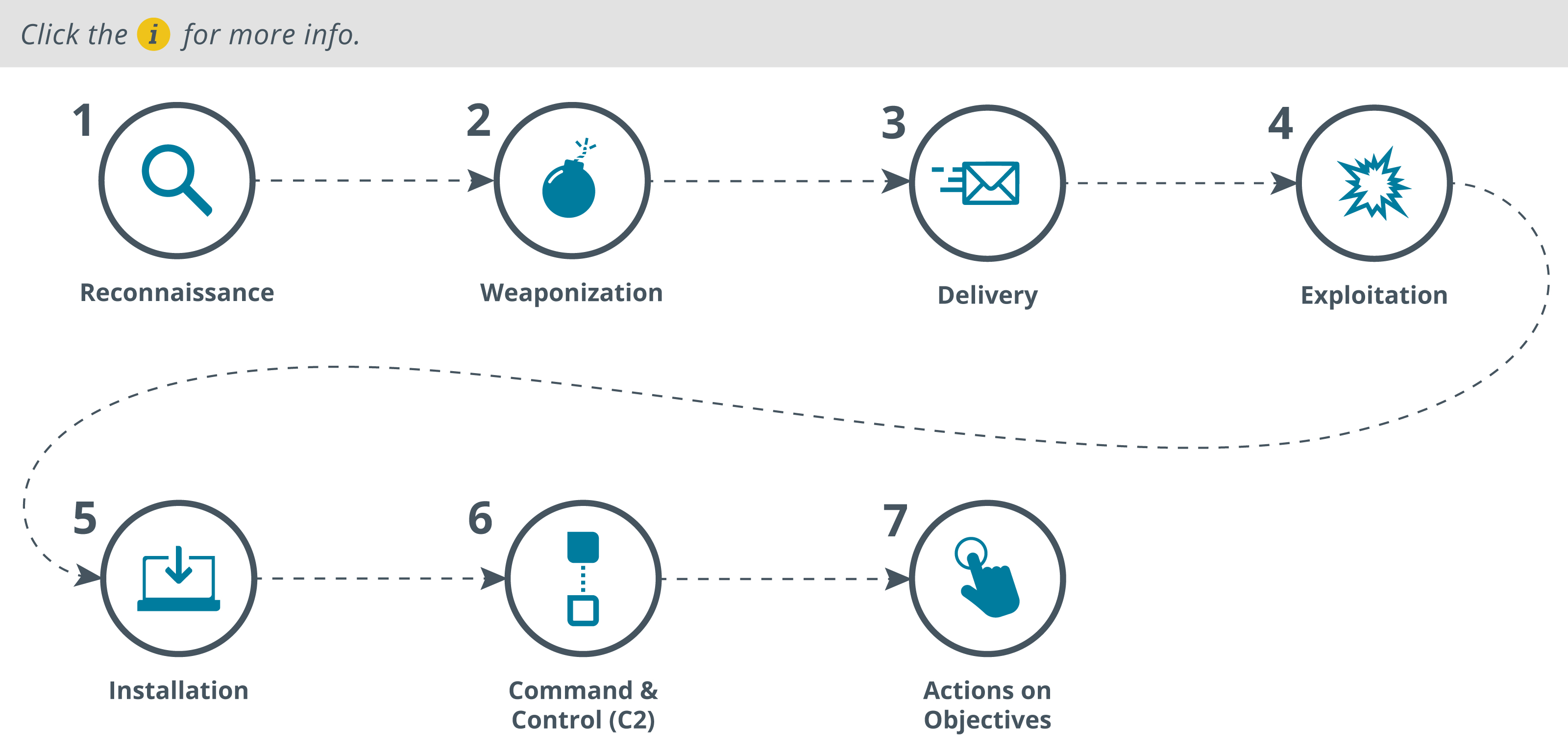
Cyber Kill Chain
A framework that describes the stages of a cyber attack
- Reconnaissance
- Scoping out the target
- Weaponization
- Preparation of attack based on recon from previous step
- Could be payload code + exploit code
- Delivery
- Weaponized code is transmitted to target system
- Exploitation
- Weaponized code is executed on the system
- Installation
- Weaponized code runs a remote access tool (RAT) and achieves persistence on target system
- Command and control
- Outbound channel is established to remote server that allows the attacker to control the RAT
- Actions on objectives
- Access is used to collect information and exfiltrate information from target
- There could be other goals or motives
See Also: MITRE ATT&CK and Diamond Model